COPY PASTE EDIT REPEAT
This write up will be a lot less talk and a lot more action. There are a lot of tutorials out there but if you need some better in-depth info, I highly recommend the BIND documentation that ISC has put together. They really have done a fantastic job.
Little note before we get rolling. This setup will allow for being a caching server or all the way to being authoritative (be your own name server). The config files below will have all the meat required to be authoritative, but will be commented out. The initial setup will just be caching. This will give you time to get the system all setup and start using the system, then you can go back through and uncomment the parts you want to use.
I have used this setup for many many years and it has treated me well.
Here comes a warning...
As you copy and paste these configs into your system, please be sure to check it over real good and change names and IP's to fit your setup. It may require some digging around if you miss something. Just a heads up!
And here we go!
setupwillbeHere
jailedisintoa/opt/namedquick- folder and file
structure:drill down.
All of this will be created with the script/configs. minus the files that get generated automatically.
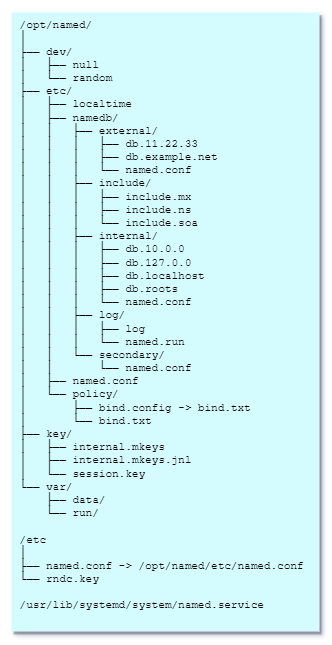
FILES (current as of 2023.07.20):
DOCUMENT - https://downloads.isc.org/isc/bind9/9.18.17/doc/arm/Bv9ARM.pdf
BIND 9.18.17 - https://downloads.isc.org/isc/bind9/9.18.17/bind-9.18.17.tar.xzCREATE "NAMED" USER:
mkdir /etc/empty groupadd -g 25 named useradd -g named -u 25 -d /opt/named -m -k /etc/empty -s /bin/false -c "BIND9" namedCREATE JAIL STRUCTURE:
mkdir /opt/named && cd /opt/named && mkdir -p dev etc/namedb var/{run,data} && mkdir -p /opt/named/etc/namedb/{include,internal,external,secondary,log}├──&& mkdir -p /opt/named/etc/policy && mknod /opt/named/dev/│ ├──null│c└──1 3 && mknod /opt/named/dev/random├──c 1 8 && chmod 666 /opt/named/dev/{null,random} && cp /etc/│ ├──localtime│/opt/named/etc├──&&namedb/chown│-R│named.named├──/opt/namedexternal/COPY
│CRYPTO│POLICY│TO├──JAIL:db.11.22.33cp│/usr/share/crypto-policies/DEFAULT/bind.txt│/opt/named/etc/policy│cd├──/opt/named/etc/policydb.example.netln│-s│bind.txt│bind.config└──DOWNLOAD AND EXTRACT ARCHIVE:
cd /opt wget https://downloads.isc.org/isc/bind9/9.18.17/bind-9.18.17.tar.xz gtar -xf bind-9.18.17.tar.xz rm -f bind-9.18.17.tar.xzGRAB DEPENDENCIES (building with GeoIP2, XML, JSON, LMDB, IDN):
dnf -y install gcc libgcc glibc-devel jemalloc jemalloc-devel \ json-c-devel keyutils-libs-devel krb5-devel libcap-devel \ libcom_err-devel libedit-devel libidn2-devel libmaxminddb \ libnghttp2-devel libselinux-devel libsepol-devel libuv-devel \ libverto-devel libxcrypt-devel libxml2-devel lmdb-devel \ ncurses-devel openssl-devel pcre2-devel pcre-devel \ readline-devel xz-devel zlib-devel libmaxminddb-develBUILD CONFIG:
cd /opt/bind-9.18.17 ./configure \ --with-libidn2 \ --with-libxml2 \ --with-json-c \ --with-lmdb \ --enable-geoip \ --with-maxminddb \ --with-openssl \ --disable-static \ --prefix=/usr \ --sysconfdir=/etc \ --localstatedir=/var \ --enable-full-reportMAKE AND INSTALL:
make && make installGENERATE RNDC.KEY (will be placed in /etc):
rndc-confgen -a -b 512This next part is two pieces. Need to copy the key out of the rndc.key and plug it into the named.conf
│file.│├──Youinclude/could│copy│the│entire├──contentsinclude.mxof│the│rndc.key│as├──wellinclude.nsand│just│replace│the└──entireinclude.soablock│in│the├── internal/ │ │ │ ├── db.10.0.0 │ │ │ ├── db.127.0.0 │ │ │ ├── db.localhost │ │ │ ├── db.roots │ │ │ └── named.conf │ │ ├── log/ │ │ │ ├── log │ │ │ └── named.run │ │ └── secondary/ │ │ └── named.conf │ ├── named.conf │ └── policy/ │ ├── bind.config->file.bind.txt│└──CREATE
bind.txtMAIN├──NAMED.CONFkey/FILE:│cat├── internal.mkeys │ ├── internal.mkeys.jnl │ └── session.key └── var/ | ├── data/ | └── run/ | | └──/etc | ├── named.conf -> /opt/named/etc/named.conf|<<└──"EOF" ### BIND 9.18.17 - MAIN CONFIG acl "internals" { 127.0.0.1; }; options { directory "/etc/namedb"; dump-file "/var/data/named.db"; /* rndc dumpdb */ statistics-file "/var/data/named.stats"; /* rndc stats */ memstatistics-file "/var/data/mem.stats"; /* writes on exit */ secroots-file "/var/data/named.secroots"; /* rndc secroots */ recursing-file "/var/data/named.recursing"; /* rndc recursing */ pid-file "/var/run/named.pid"; version "[secured]"; max-cache-size 10%; listen-on port 53 { 127.0.0.1; }; listen-on-v6 { none; }; #forwarders { 1.1.1.1; 9.9.9.9;}; allow-query { 127.0.0.1; }; #querylog no; managed-keys-directory "/key"; session-keyfile "/key/session.key"; dnssec-validation auto; #disable-empty-zone "."; include "/etc/policy/bind.config"; }; /* https://kb.isc.org/docs/aa-00769 */ #statistics-channels { # inet 127.0.0.1 port 8080 allow { 127.0.0.1; }; #}; controls { inet 127.0.0.1 port 953 allow { 127.0.0.1; } keys { rndc-key; }; }; /* copy rndc.key|here└──*/ key "rndc-key" { algorithm hmac-sha256; secret "xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx"; }; logging { channel default_debug { file "log/named.run"; print-time yes; print-category yes; print-severity yes; severity dynamic; }; channel my_log { file "log/log"; print-time yes; print-category yes; print-severity yes; severity info; }; channel my_lame { file "log/lame"; print-time yes; print-category yes; print-severity yes; severity info; }; channel my_xfer { file "log/xfer"; print-time yes; print-category yes; print-severity yes; severity info; }; channel my_query { file "log/query"; print-time yes; print-category yes; print-severity yes; severity info; }; channel my_dnssec { file "log/dnssec"; print-time yes; print-category yes; print-severity yes; severity info; }; channel my_ddns { file "log/ddns"; print-time yes; print-category yes; print-severity yes; severity info; }; channel my_client { file "log/client"; print-time yes; print-category yes; print-severity yes; severity info; }; channel my_auth { file "log/auth"; print-time yes; print-category yes; print-severity yes; severity info; }; category default { my_log; default_debug; }; category general { my_log; default_debug; }; category config { my_log; default_debug; }; category network { my_log; default_debug; }; category zoneload { my_log; default_debug; }; category dispatch { my_log; default_debug; }; category queries { my_query; default_debug; }; category query-errors { my_query; default_debug; }; category lame-servers { my_lame; default_debug; }; category edns-disabled { my_lame; default_debug; }; category notify { my_xfer; default_debug; }; category xfer-in { my_xfer; default_debug; }; category xfer-out { my_xfer; default_debug; }; category security { my_client; default_debug; }; category client { my_client; default_debug; }; category dnssec { my_dnssec; default_debug; }; category update { my_ddns; default_debug; }; category update-security { my_ddns; default_debug; }; category resolver { my_auth; default_debug; }; category cname { my_auth; default_debug; }; category delegation-only { my_auth; default_debug; }; }; view "internal" { match-clients { localhost; internals; }; allow-recursion { localhost; internals; }; allow-transfer { none; }; include "internal/named.conf"; }; //view "external" { // match-clients { any; }; // allow-recursion { none; }; // //include "external/named.conf"; //include "secondary/named.conf"; //}; EOFCOPY RNDC.KEY CONTENTS INTO NAMED.CONF (the block looks exactly the same as the key file):
cat /etc/rndc.keykey "rndc-key" {
algorithm hmac-sha256;
secret "xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx";
};LINK MAIN NAMED.CONF TO /ETC;
ln -s /opt/named/etc/named.conf /etc/named.confCHANGE TO INCLUDE FOLDER AND CREATE INCLUDE FILES (change files to reflect your setup):
cd /opt/named/etc/namedb/include cat > include.soa << "EOF" ; ; SOA Record ; $TTL 28800 ; *** THERE ARE DOTS ON THE ENDS OF THESE AND NO @ ON THE EMAIL ADDRESS *** @ IN SOA servername.example.com. emailuser.example.com. ( 2023072001 ; serial 10800 ; refresh 3600 ; retry 604800 ; expire 86400 ) ; minimum EOF cat > include.ns << "EOF" ; ; Name Server Record ; @ IN NS servername.example.com. EOF cat > include.mx << "EOF" ; ; MX Record ; @ IN MX 10 mailserver1.example.com. @ IN MX 20 mailserver2.example.com. EOFCHANGE TO INTERNAL FOLDER AND CREATE LOCAL/INTERNAL ZONES AND CONFIG FILE:
cd /opt/named/etc/namedb/internal cat > db.localhost << "EOF" ; ; LOCALHOST FORWARD ZONE ; $include "include/include.soa" $include "include/include.ns" localhost. IN A 127.0.0.1 EOF cat > db.127.0.0 << "EOF" ; ; LOCALHOST REVERSE ZONE ; $include "include/include.soa" $include "include/include.ns" 1 IN PTR localhost. EOF cat > db.example.com << "EOF" ; -----> example.com <----- //$include "include/include.soa" //$include "include/include.ns" //$include "include/include.mx" ; ; Host Addresses and Canonical Names ; ;@ IN A 10.0.0.2 ;www IN CNAME @ ;ftp IN CNAME @ //router A 10.0.0.1 //dnsserver A 10.0.0.2 //server1 A 10.0.0.3 //server2 A 10.0.0.4 //pc1 A 10.0.0.5 //pc3 A 10.0.0.6 //sweetname CNAME server1 EOF cat > db.10.0.0 << "EOF" ; -----> example.com - Reverse Zone: 0.0.10.in-addr.arpa. <----- //$include "include/include.soa" //$include "include/include.ns" ; INTERNAL SYSTEMS //1 IN PTR router.example.com. //2 IN PTR dnsserver.example.com. //3 IN PTR server1.example.com. //4 IN PTR server2.example.com. //5 IN PTR pc1.example.com. //6 IN PTR pc2.example.com. EOF cat > named.conf << "EOF" zone "." { type hint; file "internal/db.roots"; }; zone "localhost" { type master; file "internal/db.localhost"; notify no; }; zone "0.0.127.in-addr.arpa" { type master; file "internal/db.127.0.0"; notify no; }; // zone "example.com" { // type master; // file "internal/db.example.com"; // allow-update { key "rndc-key"; }; // notify yes; // }; // zone "0.0.10.in-addr.arpa." { // type master; // file "internal/db.10.0.0"; // allow-update { key "rndc-key"; }; // notify yes; // }; EOFCHANGE TO SECONDARY FOLDER AND CREATE SAMPLE CONFIG:
cd /opt/named/etc/namedb/secondary cat > named.conf << "EOF" // SECONDARY ZONE FILE //zone "example.net" { // type slave; // masters { master ns ip address here; }; // file "secondary/db.example.net"; //}; EOFCHANGE TO EXTERNAL FOLDER AND CREATE SAMPLE CONFIGS:
cd /opt/named/etc/namedb/external cat > named.conf << "EOF" // EXTERNAL FORWARD ZONES //zone "example.org" { // type master; // file "external/db.example.org"; // notify no; //}; // EXTERNAL REVERSE ZONES //zone "33.22.11.in-addr.arpa." { // type master; // file "external/db.11.22.33"; // notify no; //}; EOF cat > db.example.org << "EOF" ; -----> example.org <----- $include "include/include.soa" $include "include/include.ns" $include "include/include.mx" ; ; Host Addresses and Canonical Names ; @ IN A 11.22.33.44 www IN CNAME @ ftp IN CNAME @ EOF cat > db.11.22.33 << "EOF" ; -----> example.org - Reverse Zone: 33.22.11.in-addr.arpa. <----- $include "include/include.soa" $include "include/include.ns" 44 IN PTR example.org. EOFCREATE SYSTEMD SERVICE:
cat > /usr/lib/systemd/system/named.service << "EOF" [Unit] Description=Berkeley Internet Name Domain (DNS) Wants=nss-lookup.target Before=nss-lookup.target After=network.target [Service] Type=forking Environment=NAMEDCONF=/etc/named.conf EnvironmentFile=-/etc/sysconfig/named ExecStart=/usr/sbin/named -u named -t /opt/named -c ${NAMEDCONF} $OPTIONS ExecReload=/usr/sbin/rndc null > /dev/null 2>&1; then /usr/sbin/rndc reload ExecStop=/usr/sbin/rndc stop > /dev/null 2>&1 PrivateTmp=true [Install] WantedBy=multi-user.target EOF
CREATE
OPTION - folder and file
cat > /etc/sysconfig/named << "EOF"
# BIND named process options
# ~~~~~~~~~~~~~~~~~~~~~~~~~~
#
# OPTIONS="whatever" -- These additional options will be passed to named
# at startup. Don't add -t here, enable proper
# -chroot.service unit file.
#
# NAMEDCONF=/etc/named/alternate.conf
# -- Don't use -c to change configuration file.
# Extend systemd named.service instead or use this
# variable.
#
# DISABLE_ZONE_CHECKING -- By default, service file calls named-checkzone
# utility for every zone to ensure all zones are
# valid before named starts. If you set this option
# to 'yes' then service file doesn't perform those
# checks.
OPTIONS="-4"
EOFCREATE SCRIPT TO UPDATE ROOTS FILE AND RUN IT:
cat > /opt/named/etc/namedb/update_roots << "EOF"
#!/bin/bash
# TRY DIG IF WGET FAILS
# dig @a.root-servers.net . ns > /opt/named/etc/namedb/internal/db.roots
wget --user=ftp --password=ftp ftp://ftp.internic.net/domain/named.cache -O /opt/named/etc/namedb/internal/db.roots
chown named.named /opt/named/etc/namedb/internal/db.roots
exit
EOF
chmod +x /opt/named/etc/namedb/update_roots
/opt/named/etc/namedb/update_roots
CREATE SCRIPT TO RELOAD BIND AND TAIL THE LOG FILE (ctrl+c to drop the tail after running the script):
cat > /opt/named/etc/namedb/reload_bind << "EOF"
#!/bin/bash
### WIPES LOG FILES ###
rm -f /opt/named/etc/namedb/log/*
touch /opt/named/etc/namedb/log/log
touch /opt/named/etc/namedb/log/named.run
chown -R named.named /opt/named
systemctl stop named
sleep 2
systemctl start named && tail -f /opt/named/etc/namedb/log/named.run
exit
EOF
chmod +x /opt/named/etc/namedb/reload_bind
FIX UP SOME PERMISSIONS:
chown root:named /etc/rndc.key /etc/named.conf
chmod 640 /etc/rndc.key /etc/named.conf
chown -R named.named /opt/named
After all that copy'n and paste'n, you should be ready to go.
Make sure all your data is correct in the files. Once validated, start it up!
RE-READ SYSTEMD, ENABLE, AND START BIND:
systemctl daemon-reload
systemctl enable named
systemctl start namedCHANGE YOUR RESOLVE FILE AND TEST:
cp -a /etc/resolv.conf /etc/resolv.conf.bak
cat > /etc/resolv.conf << "EOF"
nameserver 127.0.0.1
EOF
# FORWARD TEST
dig a cloudflare.com
# REVERSE TEST
dig -x 1.1.1.1
That's it!
I hope this write up and these configs, love you long time. :)
